Related Posts
Subscribe via Email
Subscribe to our blog to get insights sent directly to your inbox.
By: Tony Sweet
Phishing attacks are one of the most common attack vectors that attempt to compromise your personal data. Phishing is not very expensive or time intensive which makes it so popular among cybercriminals.
Phishing attacks are usually in the form of a spoofed email or website. The attacker usually copies a reputable website such as a bank and then sends an email appearing like it is from a reputable source with links that redirect the unsuspecting user to their website. The email usually has some sort of urgency such as “Your account could be compromised, click here to review your recent transactions.” When a user clicks the link they are directed to what appears to be their bank but in reality is the cybercriminals similar looking website. If the user enters their credentials to log in, it will send those credentials to the attacker, thus compromising your personal data.
Other examples of this are fake order forms trying to compromise your credit card, social security number, or other confidential information. The attack can also try to collect information about your computer system, or infect it with malware.
Anti-Virus software does not protect you from most phishing attacks. It is up to the user to learn how to spot phishing attacks and protect their own personal data.
Phishing Links are disguised as a reputable link that actually redirects the user to a different page. These are commonly found in Emails and on Social Media.

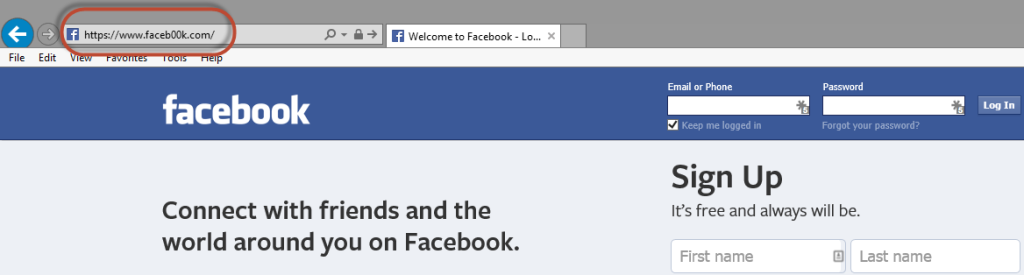
Spoofed Website's can look like a reputable site that you use (Facebook, LinkedIn, Banking Websites, etc.) but have slightly altered URL’s. For instance you could think you’re on facebook.com because it looks just like Facebook but in reality you are on faceb00k.com (zeros instead of o’s). Once you enter your login information it sends your information to the cybercriminal and redirects you to the real website. They cannot fully compromise your account, and possibly more if you use the same email and password on multiple accounts.
Spoofed Email’s appear to come from an authority’s source but are usually generic in nature. A common example would be receiving an email from your IT department about a recent virus, and directing you to click a link in order to protect your computer. IT departments would every ask you to do this yourself.
If you have been phished you should change your passwords, contact your credit card company and request a new card, and monitor your credit score if your social security number has been compromised.
Protect yourself by using different passwords on every site, especially financial services such as online banking accounts, investment accounts, or e-commerce accounts. Password managers such as LastPass and KeePass can help maintain multiple passwords in a secure way.

Justin (he/him) is the founder and CEO of NuHarbor Security, where he continues to advance modern integrated cybersecurity services. He has over 20 years of cybersecurity experience, much of it earned while leading security efforts for multinational corporations, most recently serving as global CISO at Keurig Green Mountain Coffee. Justin serves multiple local organizations in the public interest, including his board membership at Champlain College.
Subscribe to our blog to get insights sent directly to your inbox.