There’s a big difference between a security assessment and a security program review. The NIST Cybersecurity Framework is the leading go-to for developing a security program. The NIST Cybersecurity Framework is broken down into three parts:
- Framework Core
- Implementation Tiers
- Profiles
Need assistance getting started with the NIST Cybersecurity Framework and maturing your security processes? Contact NuHarbor today!
The Core provides a set of desired cybersecurity activities and outcomes and creates a common language. You Think of this as core capabilities implemented in a way that everyone can understand and talk about.
The second part is the Implementation Tiers, which guide organizations to consider the appropriate rigor of security-based company strategic goals and objectives. You can think of this of as a maturity model for your organization that considers executive risk appetite. Simply put, it measures where you’re at today and gives you a framework to decide how good you want to be in the future.
The third and final part is Profiles, which is about optimizing the cybersecurity framework to best serve the organization. The Framework is voluntary, so there is no ‘right’ or ‘wrong’ way to do it. One way of approaching Profiles is for an organization to map their cybersecurity requirements, mission objectives, and operating methodologies, along with current practices, against the subcategories of the Framework Core to create a “Current” Profile. These requirements and objectives can be compared against the current operating state of the organization to gain an understanding of the gaps between the two. Profiles help to create a prioritized implementation plan based on risk, priority, budget, timing.
As you get started with the NIST Cybersecurity Framework to establish your security program, it can be overwhelming. If you’re unsure how or where to start, start with the Core. Once you get comfortable with the Core, then you can start taking on the Tiers and Profiles.
The Core
Let’s start with breaking down the Core. The Core consists of three parts:
- Functions (5 total)
- Categories (23 total)
- Subcategories (108 total)
Simply put, this is a way to organize the logical groupings of the NIST CSF functions and capabilities so you can perform logical mappings between the security controls and desired functions and vise-versa.
The Core Functions
The Core includes five high level functions:
- Identify
- Protect
- Detect
- Respond
- Recover
1. Identify
The Identify function assists in developing your ability to manage your security program related to governance of the program and manage over cybersecurity risk. This function also assists in developing an organizational understanding of managing cybersecurity risk as it pertains to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus on and prioritize its efforts, consistent with its risk management strategy and business needs.
2. Protect
The Protect function establishes core safeguards to protect and ensure delivery of core services. Performed correctly, this function will also give you the ability to limit or contain the impact of a potential cybersecurity event.
3. Detect
The Detect function defines the appropriate activities for identifying a cybersecurity event. Developing this function allows you to quickly identify and respond quickly to a cybersecurity event for effective containment. Your ability to Detect directly affects your ability to timely exercise the Respond function.
4. Respond
The Respond function includes a series of actions and activities for effectively taking action regarding a detected cybersecurity incident. The Respond function supports the ability to contain the impact of a potential cybersecurity incident.
5. Recover
The Recover function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover function supports timely recovery to normal operations to reduce the impact of a cybersecurity incident.
These five functions are not only applicable to cybersecurity risk management, but also to risk management at large.
The Core Categories
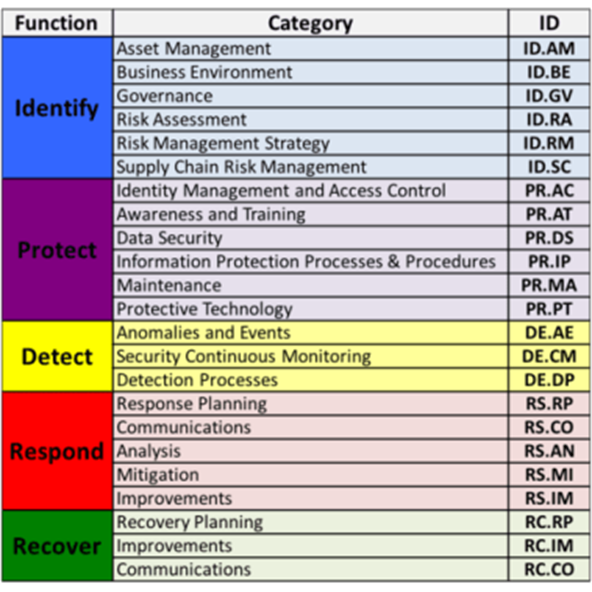
The next level down is the 23 Categories that are split across the five Functions.
This image depicts the Framework Core’s Functions and Categories:
A Short Description of Categories
- Asset Management: The organization identifies data, personnel, devices, systems, and facilities that enable the organization and achieve business goals.
- Business Environment: The organization’s mission, objectives, stakeholders, and activities are understood and prioritized. This information is used to inform cybersecurity roles, responsibilities, and risk management decisions.
- Governance: The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk.
- Risk Assessment: The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals.
- Risk Management Strategy: The organization’s priorities, constraints, risk tolerances, and assumptions are established and used to support operational risk decisions.
- Supply Chain Risk Management: Identifies, establishes, and assesses cyber supply chain risk management and gains stakeholder agreement.
- Identity Management and Access Control: Access to assets and associated facilities is limited to authorized users, processes, or devices, and to authorized activities and transactions.
- Awareness and Training: The organization’s personnel and partners are provided cybersecurity awareness education and are adequately trained to perform their information security-related duties and responsibilities consistent with related policies, procedures, and agreements.
- Data Security: Information and records (i.e., data) are managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
- Information Protection Processes and Procedures: Security policies (that address purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities), processes, and procedures are maintained and used to manage protection of information systems and assets.
- Maintenance: Maintenance and repairs of industrial control and information system components is performed consistent with policies and procedures.
- Protective Technology: Technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
- Anomalies and Events: Anomalous activity is detected in a timely manner and the potential impact of events is understood.
- Security Continuous Monitoring: The information system and assets are monitored at discrete intervals to identify cybersecurity events and verify the effectiveness of protective measures.
- Detection Processes: Detection processes and procedures are maintained and tested to ensure timely and adequate awareness of anomalous events.
- Response Planning: Response processes and procedures are executed and maintained to ensure timely response to detected cybersecurity events.
- Communications (Respond): Response activities are coordinated with internal and external stakeholders, as appropriate, to include external support from law enforcement agencies.
- Analysis: Analysis is conducted to ensure adequate response and support recovery activities.
- Mitigation: Activities are performed to prevent expansion of an event, mitigate its effects, and eradicate the incident.
- Improvements: Organizational response activities are improved by incorporating lessons learned from current and previous detection/response activities.
- Recovery Planning: Recovery processes and procedures are executed and maintained to ensure timely restoration of systems or assets affected by cybersecurity events.
- Improvements: Recovery planning and processes are improved by incorporating lessons learned into future activities.
- Communications (Recover): Restoration activities are coordinated with internal and external parties, such as coordinating centers, Internet Service Providers (ISPs), owners of attacking systems, victims, other CSIRTs, and vendors.
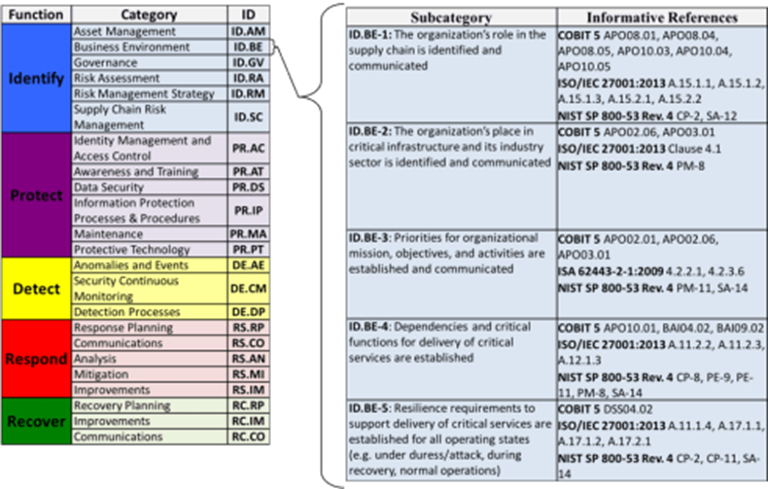
The Core Subcategories
After Categories, there are 108 Subcategories. As we go from Function (i.e., capability) to Category to Subcategory, we get a little more granular with each step and level we go down.
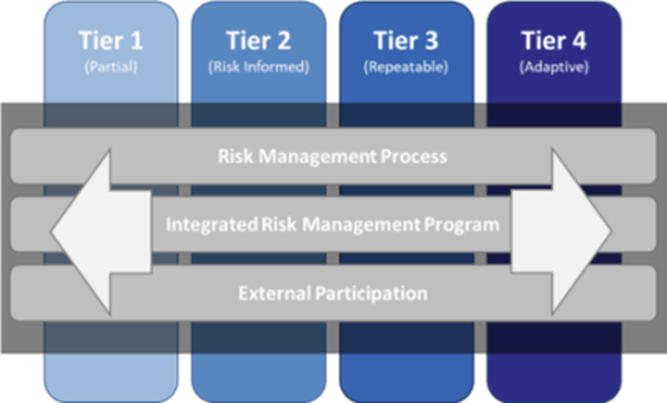
Framework Implementation Tiers
Framework Implementation Tiers (“Tiers”) describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework. The Tiers include:
- Partial (Tier 1)
- Risk Informed (Tier 2)
- Repeatable (Tier 3)
- Adaptive (Tier 4)
Tiers provide context on how an organization views cybersecurity risk and the organizational processes in place to manage that risk. The Tiers describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework (e.g., risk and threat aware, repeatable, and adaptive). The Tiers characterize an organization’s practices over a range, from Partial (Tier 1) to Adaptive (Tier 4), and reflect a progression from informal, reactive responses to approaches that are agile and risk informed. During the Tier selection process, an organization should consider its current risk management practices, threat environment, legal and regulatory requirements, business/mission objectives, and organizational constraints.
The Core Profile
Overview of Profiles
As an organization determines how to use the Cybersecurity Framework Core to assist in managing their cybersecurity risks, they can develop organization-specific Profiles to map their current state and a desired future state based on their goals and mission.
The following excerpt from the Cybersecurity Framework describes Profiles:
“Through use of the Profiles, the Framework will help the organization align its cybersecurity activities with its business requirements, risk tolerances, and resources.
. . . A Framework Profile (“Profile”) represents the outcomes based on business needs that an organization has selected from the Framework Categories and Subcategories. The Profile can be characterized as the alignment of standards, guidelines, and practices to the Framework Core in a particular implementation scenario. Profiles can be used to identify opportunities for improving cybersecurity posture by comparing a “Current” Profile (the “as is” state) with a “Target” Profile (the “to be” state).”
Tailoring a Profile
Profile development tailors the Cybersecurity Framework to focus on the cybersecurity areas of particular concern to an industry, organization, or functional area as identified through its risk management processes. By evaluating the elements of the Cybersecurity Framework against a particular mission, a Profile is created that shows priorities based on evaluation of the mission against the Cybersecurity Framework Functions, Categories, and Subcategories.
Implementing and Leveraging Profiles in Organizations
The Cybersecurity Framework and Profiles provide a consistent way to discuss security objectives and activities in reader-friendly terminology that is consumable for multiple roles, from executives to technical implementers. Within organizations, benefits include describing how security investments will be used to a Board of Directors and measuring progress in meeting cybersecurity objectives year over year. Advantages provided by industry-focused Profiles include defining consistent priorities across a sub-sector and enabling conversations by discussing security activities using consistent terminology. Industry-specific Profiles are intended to:
- Minimize future work by each organization
- Decrease the chance that organizations accidentally omit a requirement
- Encourage consistent analysis of cybersecurity-risk in the operational environment
- Align industry and organizational cybersecurity priorities
Organizations that are part of an industry or sub-sector that has one or more industry-focused Profiles generally use those industry-focused Profiles to inform decisions made when constructing their organization-focused Profiles and measuring progress.
NuHarbor is a leading national cybersecurity services firm, supporting the diverse needs of hundreds of clients with clear, comprehensive, and outcome-based solutions. Our tenured, highly certified Security Advisory Team averages 10 years of compliance and information assurance experience and maintains a strong focus on the National Institute of Standards and Technology (NIST). If you need assistance with the NIST Cybersecurity Framework, or any security framework, contact us today!
Included Topics

Justin (he/him) is the founder and CEO of NuHarbor Security, where he continues to advance modern integrated cybersecurity services. He has over 20 years of cybersecurity experience, much of it earned while leading security efforts for multinational corporations, most recently serving as global CISO at Keurig Green Mountain Coffee. Justin serves multiple local organizations in the public interest, including his board membership at Champlain College.