Over the last few years, I’ve seen many different types of security organizations. Some centralize IT security, others have a hybrid structure with some security technology under other under IT infrastructure, and some are very lightweight. I’ve only seen one scenario in which a CISO was a respected C-level executive reporting to the CEO, had responsibility for maintaining information security strategy, and had direct reports to help translate that strategy into the execution of IT security operations. I think of it as the time I saw the security unicorn. The security strategy worked perfectly – it was aligned with the CEO’s strategy and could be turned on a dime. I thought to myself, this is how security should be managed and this is how all security shops should be set up. Below is my proposal for how all security departments should be configured.
1. The Security Industry is Evolving
Over the past couple years, we’ve seen the security industry grow a lot. We’re a young profession working our way through the growing pains of helping our business organizations determine what “information security” and “IT security” should be and how to best help the businesses we work for (See blog post: The Difference Between Information Security and IT Security). To add to the growing pains, the security profession must grapple with an increasingly complex threat landscape as our role becomes more visible and expectations increase. The issue becomes even bigger when security teams are asked to do more despite static headcount and budgets. According to ZDNet’s security budget survey 41% of IT security departments will see budget increases in 2014 (which is a 16% positive response increase over 2013). But, 2014 IT budgets overall are increasing, and according to Network World’s IT Budget Survey, 65% of IT departments will see an overall increase. TripWire estimates the average increase to be 4.06%. So, security budgets are increasing but not at the rate of average IT budgets.
The demand for IT security professionals far outweighs the supply. I often hear there’s a gap in the security talent pool, and I understand that we all want to hire the best talent, but we can’t all be the New York Yankees and Boston Red Sox. Sometimes you have to be the Oakland Athletics and build your team from a group of people simply interested in playing the game. The time to develop our talent is now, and we need to teach how security should be done so the legacy can be carried forward.
2. CISOs Are (Finally) Being Seen as Business Advisor
The good news is we’re seeing the rise of the Chief Information Security Officer (CISO). This is a happy evolution – we’ve struggled for so long to find business executives versed in cybersecurity, and now we finally have folks talking about security in terms that CEOs and Boards can relate to. We’re getting the right players in place to successfully lead Security Organization 2.0.
3. Precious and Limited Security Talent is Burning Out
Unfortunately, I see many CISOs offloading operational IT security responsibilities to other IT departments so they can focus on information security. Admittedly, a CISO should be focused on strategy, but accountability with no responsibility creates a very stressful work environment and it’s why we see high rates of burnout in the security profession, especially among IT security staff.
More and more I’m seeing security operations shouldered by IT applications and infrastructure teams because the security department doesn’t have the personnel to support enterprise-level security operations. This leads to IT departments being responsible for systems availability in addition to security, and sometimes that’s a conflict of interest. Managing security technology requires a specific skill set, crafted attention to detail, and constant care and feeding. IT security technology is set it and forget it. IT security should be centralized under a CISO and for the development of core competencies.
4. A CIO or CFO Would Never Survive in the Security Paradigm
What if our CIOs and CFOs had to struggle with the same issues that security deals with (i.e., managing a strategy with distributed operations)? How effective would these functions be? What if CIOs just led a strategy and each business unit was responsible for establishing their own technology platforms (it’s called shadow IT and it’s a problem). Businesses would suffer from wasted time, inconsistent business logic, an inconsistent approach, wasted investment, business inefficiencies, high risk of information sprawl, barriers to enhancement, and organizational dysfunction. It would be a disaster and a waste of resources – we’d ask, is the CIO job too big for one person? Imagine if CFOs were in the same position. Balance sheets would be disorganized and incomplete. We’d be sitting ducks to shareholder lawsuits because of inaccurate and misleading financial statements, and our businesses would struggle to determine cash flow month over month.
Why should security be any different?
5. IT Staff Aren’t IT Security (or Information Security) Professionals.
Most IT security professionals are born out of love for the profession. We’re self-taught. There’s no fancy security MBA (although that would be neat). Some of the best security professionals I’ve ever worked with don’t have any fancy certificates or degrees, but they are voracious consumers of information and read everything. IT staff, such as network engineers, are focused on network routing, switching, and telecommunications. I’ve never seen a network engineer spend time researching zero-day malware and inserting that signature into an IPS device to prevent potential infection – that’s a security job. I’ve also never seen a database administrator (DBA) research new SQL injection attacks or worry about transparent data encryption; DBAs are focused on schema architecture and performance tuning. Not to say network engineers or DBAs don’t take a periodic interest in security, but their job is not security, it’s service delivery, and they’re evaluated on the delivery of their service not how secure everything is.
Security technology should be a coordinated effort – threat and vulnerability management should tie into security device management, which should tie into security engineering, which should be tied to policies and security architecture. This coordination usually takes a very focused and dedicated perspective on the security trade.
The Security Organization 2.0 Solution
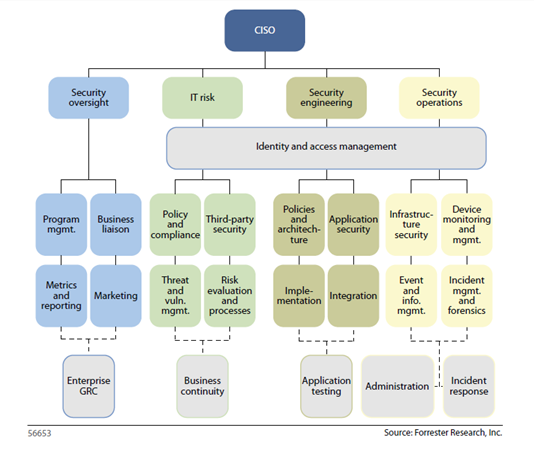
First, I need to thank Forrester for the fantastic graphic below. To summarize this model, the CISO is a peer to other C-levels and helps to mature security strategy based on business goals and objectives. The CISO needs to have direct reports who can help translate business strategy into IT security strategy. These individuals also need to backfill the CISO by establishing relationships with business peers. A key point here is that all information security and IT security operations report into the CISO. This helps to ensure that a CISO can maintain the integrity of their security and compliance architectures, and that integrity of the environment isn’t threated in the name of service availability. As former CISO in a distributed security model, I once learned that the company’s security perimeter was sacrificed for something as simple as adding a web server to a PCI network segment to increase processing capacity. For the all the PCI-gurus out there, you know that these types must be handled in a very specific way to maintain compliance. However, if my staff had been responsible for firewalls, we would have known about the change beforehand instead of finding out a couple days later.
This is a great model. Forrester did a great job documenting details of the graphic. For additional details on what each pillar is and does, refer back to the Forrester white paper.
This model could also extend to a Chief Security Officer (CSO) by adding a pillar for physical security to develop a converged security model.
Included Topics

Justin (he/him) is the founder and CEO of NuHarbor Security, where he continues to advance modern integrated cybersecurity services. He has over 20 years of cybersecurity experience, much of it earned while leading security efforts for multinational corporations, most recently serving as global CISO at Keurig Green Mountain Coffee. Justin serves multiple local organizations in the public interest, including his board membership at Champlain College.


