I was reflecting back to my Sun Microsystems days this morning, for some very odd reason my mind went to a time when Greg Papadopoulos (our then Chief Technology Officer) spoke about his Red Shift Theory. The idea of Mr Papadopolous' theory was that, and I quote from Information Week: "that an elite group of companies are consuming inordinate amounts of IT infrastructure, well beyond most other businesses, and that their demand is growing exponentially." Mr Papadopolous called this idea of expanding (growing) companies the "Red Shift Theory". This parallels the idea that, quoted from Information Week " In astronomy, the term refers to what happens to the wavelength of light emitted from an object traveling away from the observer: It lengthens, moving to the redder end of the visible spectrum." When I heard Mr Papadopoulos' talk, one thing he mentioned (which isn't covered in the Information Week Red Shift Theory Article), is the services that these companies were providing would be the popular services of the future. Looking back he was spot on, I recall his short list was Amazon, Google, Youtube, MySpace (pre-Facebook), and few others I can't remember. The services these companies offered are still popular today, and maybe even evolved more. The opposite of Red Shift is Blue Shift, and in summary all other companies not Red Shift are Blue Shift that will grow at the rate of GDP. Mr Papadopolous, if you ever read this I hope I did your Red Shift Thoery justice.
Naturally I wondered "does Information Security have a Red Shift component?"
I thought about it for a bit, and resolved to a "yes!".
I've seen a lot of maturity in the Information Security corporate function over the last couple years. We've expanded beyond just IT Security and I'm seeing more Information Security departments that are mitigating business information risk (not just IT). These Information Security departments are pervasive to their companies working with HR, Finance, Marketing, Legal, and IT. The result is that more Information Security professionals are versed in business risk and are delivering Security Solutions in support of strategic business initiatives. They are also finding ways to deliver security technology in a way that extends the ability of the business innovate securely.
So...what's the Information Security Red Shift?
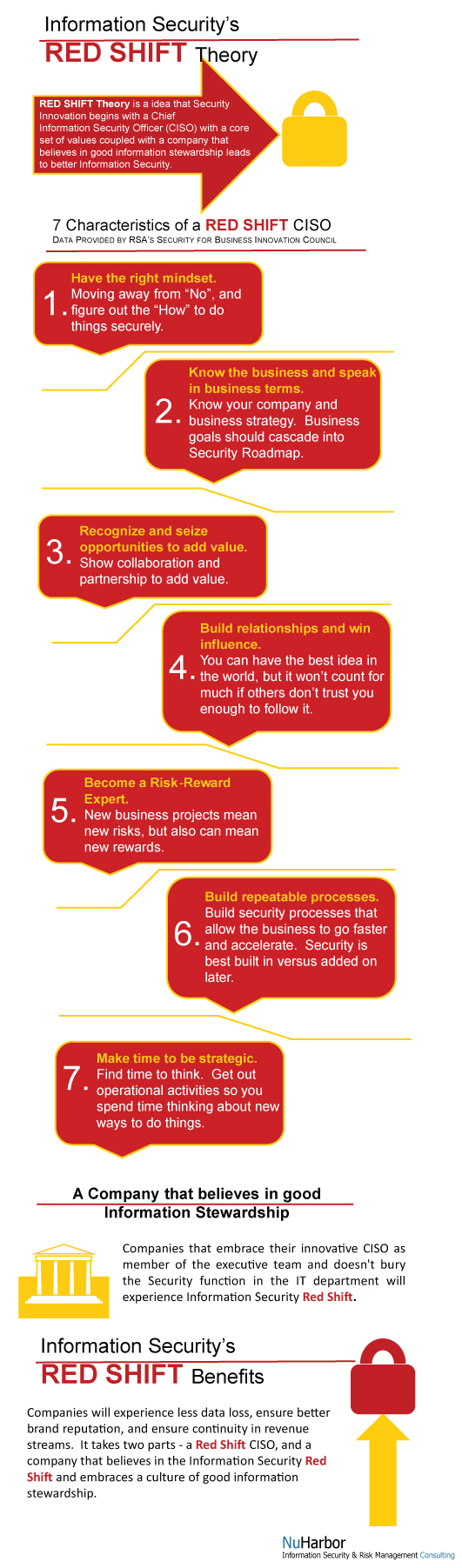
After thinking about my list for a bit, I found this list from RSA online and there's no sense in reinventing the wheel so here's the top 7 points from the RSA "Security for Business Innovation Council" in which 1000 Security Executives were interviewed about Security innovation.
1. Have the right mindset. Moving away from "No", and Figure out the "How" to do things securely.
2. Know the business and speak business. Know your business, and business strategy should cascade into the Security strategy. Figure out how to manage risks relevant to business strategy.
3. Recognize and seize opportunities to add value. Current business innovation requires advanced security solutions, use this as opportunity to engage show collaboration, partnership, and further your security agenda.
4. Build relationships and win influence. You can best idea in the world, but it won't count for much if you can't sell it and persuade others to follow it.
5. Become a Risk-Reward Expert. Taking on new business projects often means new risks. But in the course of assessing risk, be sure to assess the all rewards.
6. Build repeatable processes. Build security processes that allow the business to go faster and accelerate. Security is best built in versus tacked on later.
7. Make time to be strategic. Find time to think. Get out of the operational activities so you can spend time thinking about new ways to do things.
This list of 7 great points is only part of the Red Shift and part of the roadmap of an expanding Information Security function. The Information Security function is still evolving, and companies are still learning to embrace the Information Security function. Companies that embrace their innovative CISO as member of the executive team and doesn't bury the Security function in the IT department will experience Information Security Red Shift. These are the companies that will experience less data loss, ensure better brand reputation, and ensure continuity in revenue streams which will contribute to those companies being viable for a long time. So the Information Security Red Shift Theory is maturing, and it takes two parts - a Red Shift CISO, and a company that believes in the Information Security Red Shift and embraces a culture of good information stewardship.

Justin (he/him) is the founder and CEO of NuHarbor Security, where he continues to advance modern integrated cybersecurity services. He has over 20 years of cybersecurity experience, much of it earned while leading security efforts for multinational corporations, most recently serving as global CISO at Keurig Green Mountain Coffee. Justin serves multiple local organizations in the public interest, including his board membership at Champlain College.